5 Ways to Boost Your Router Security
New malware is targeting WiFi routers around the world. Here's what to do about it.

A new kind of malware is hitting WiFi routers around the world, and security researchers say consumers should tighten the security on their own home networks.
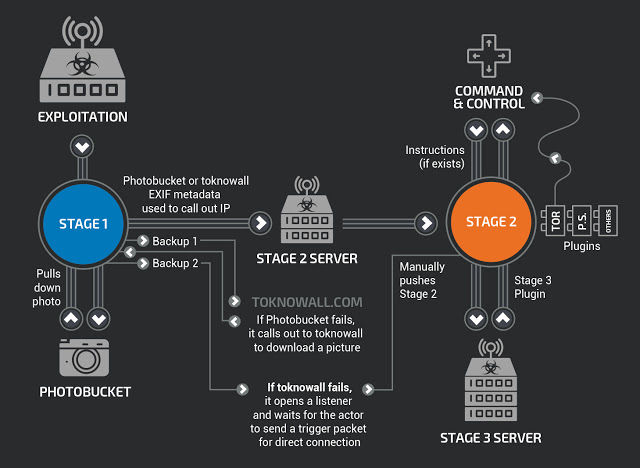
As of Wednesday, the malware, called VNPFilter, had affected half a million routers, along with certain other devices, according to Cisco's data-security group, Talos. And it had been detected in 54 countries.
More on Digital Security
"The average American could be compromised, giving attackers access to personal data and control over the device," says Cisco Talos director Craig Williams. "This is why it is crucial that consumers install security updates regularly."
Routers have long been a favorite target for hackers. In Symantec's latest annual Internet Security Threat Report, routers were the most frequently exploited type of device in IoT, or internet of things, attacks.
The devices are particularly important for consumers' security because they transmit all the data that flows in and out of the home, from emails to credit card information. VPNFilter could allow attackers to monitor data traffic, quietly use a network of routers for illegal activity, or stop either individual routers or masses of them from working at all, according to Williams.
See If You're Vulnerable to VPNFilter
Williams says his company has identified more than a dozen products that are vulnerable to the malware. Talos has published a list of the devices, near the bottom of a long, fairly technical blog post about VPNFilter. (Keep scrolling; you'll get to it.) The products listed are made by Linksys, MikroTik, Netgear, QNAP, and TP-Link.
However, the post says, "Given our observations with this threat, we assess with high confidence that this list is incomplete and other devices could be affected."
How do you know whether the malware has infected your particular router? According to both Williams and other security experts, there's no way to be sure.
"This is the scary part of router malware," says Craig Young, principal security researcher at Tripwire VERT, a security research firm. "A sophisticated attacker can create malware that would be completely undetectable by even tech-savvy end users. It is simply not possible for someone without specialized tools to confirm whether any particular router is infected or clean."
If you have one of the vulnerable devices, you should assume it has been infected, these experts say. To fix the problem, do a hard reset of the router and update the firmware, as described below.
Update Your Firmware
Router manufacturers typically roll out software updates throughout the year to address security problems. And if your router has the latest updates, you're much less likely to be infected with VPNFilter. Researchers say the malware appears to take advantage of vulnerabilities that had already been identified in the past.
If your device may have been infected, experts say, you should start by doing a hard reset, which will revert the device to the way it was when it came from the factory. Note that doing this wipes out any changes you made to your router settings.
Many routers have a button you can press for several seconds to perform the reset. You may need a paper clip to do this—router makers intentionally make it a bit tricky to avoid accidental resets. If there's no button, you may need to log into the router settings, which will also allow you to update the software.
Newer models make this relatively easy through a mobile app, which you can download to a phone, just like any other app.
For other routers, you'll need to open a web browser and type in the device's IP address. Very often, the address is 192.168.0.1 or 192.168.1.1, but this varies by brand—as do the instructions for downloading and installing your software. So do an online search for the customer support pages for your router model.
Once you perform the update, don't log out.
Instead, take some more time to really harden your defenses against future attacks. Routers are chronically ignored by many consumers, but Consumer Reports' data security and router experts say that taking the following steps can help protect you going forward.
And these steps make sense even if your device isn't vulnerable to VPNFilter.
Turn On Automatic Updates
The easiest way to make sure your router always has the newest, safest software is to set up automatic updates, which are available on many newer models. To see whether this is an option for you, check the router's companion app or look in settings.
If your router doesn't allow for automatic updates, you'll have to periodically download and install the new software from the manufacturer's website yourself.
To be safe, do this every quarter, advises Rich Fisco, who leads the router testing at Consumer Reports. You should also see whether there's a way to get security notices via email from your router's manufacturer. The best way is to complete the product registration process online, during which you'll be given the option to receive notifications when new software is available.
But eventually companies will stop releasing new software for old routers—and just when this happens varies by brand.
"If you find your router is no longer getting updates," Fisco says, "it's too risky to keep using it. Verify its status with the manufacturer, and if it has reached the 'end-of-life' stage, buy a new router."
Use Strong Passwords
If you've never done so, you should change two crucial passwords on your router: the one that lets you manage the device's settings and the one that lets you connect other devices to its wireless network.
This prevents a hacker from using a default password—or one that's easy to guess with a little online sleuthing—to access your network and potentially control your router. If that were to happen, the hacker could change your passwords, spy on you, or access the files on a network-attached hard drive.
Be sure the passwords you create are strong. They should each be comprised of at least a dozen characters, using seemingly random upper- and lower-case letters, numbers, and symbols. "Having a password people can easily guess only prevents those who are indifferent from breaking in," says Robert Richter, who oversees CR's security and privacy testing program.
Turn Off Features You Don't Use
Modern routers come with many handy features that help you manage your WiFi network, but some of them also create weak spots in your security wall. "The more things there are to poke at, the more likelihood one of them will break," Richter says.
So while you're logged into your router's settings, take a minute to review applications that could present opportunities for hackers.
If you don't use Remote Administration (also known as Remote Management or web access from WAN), make sure it's turned off. This denies access to the router's control panel from outside your home network. In most routers, the feature is off by default, but you should confirm this by visiting the advanced or administration section of the settings menu.
Disable Universal Plug-and-Play, which many home routers have enabled by default. UPnP can help devices on your home network connect to each other, but the added convenience isn't worth the security risk: This feature can make it easier for malware to spread through your network.
To disable UPnP, log into your router like you would when changing your password. Find the tools, advanced or advanced networks menu. From there, make sure the "Enable UPnP" box is unchecked.
After doing so, you may notice hiccups in the performance of certain devices on your network. You may need to retype the WiFi password into a Chromecast streaming stick, for example. But most laptops, speakers, TVs, and printers should make the transition without a hitch.
And, last, if you have a guest network without a password, disable it. You don't want unwanted guests using it without permission. Not even the neighbors' kid, who may decide to download movies illegally via your internet connection.
Install Antivirus Software
Antivirus software can protect your router—and by extension all devices connected to it—by identifying malicious software used to collect and encrypt the personal data on a computer, rendering it useless.
Just make sure you download the software from the manufacturer's official website, because scammers have been known to create fake sites. And double-check that you're not grabbing a fee-based product by mistake.
No-cost applications, such as Avira Free Antivirus, can be very effective. However, the software you pay for tends to offer extra benefits. It may provide protection against phishing schemes used by cyberthieves to trick people into giving up login credentials or financial information, for example. It may also feature antispam protection, built-in backup software, and a browser toolbar that alerts you when you're visiting a site that hosts malware.
Use WPA2
The security protocols for routers improve over time, which means the old ones get outdated. In January, for example, the Wi-Fi Alliance announced enhanced security features that will be included in the latest standard—WPA3—expected to roll out later this year.
They include simplified settings, stronger password protection, and improved data encryption.
Currently, the best security is provided by a protocol called WPA2-AES, but your router may let you use another standard, such as the older WEP protocol, instead. (Sadly, acronyms are unavoidable when discussing router security.)
In settings, make sure you have WEP turned off and WPA2-AES turned on. If you have a really old device, this may not be an option, Fisco says. "Unfortunately, router manufacturing and security research aren't always aligned," says Richter. "So older routers may not be equipped with newer protocols."
If you have one of those routers, he says, it's time to replace it.